Part 3: Apply a Terraform Plan¶
Steps¶
1. Initialize your Terraform project¶
Running the terraform init command initializes a working directory containing Terraform configuration files.
Expected output:
Bash
$ terraform init
Initializing the backend...
Initializing provider plugins...
- Finding latest version of equinix/equinix...
- Finding latest version of hashicorp/tls...
- Finding latest version of hashicorp/local...
- Installing hashicorp/local v2.4.0...
- Installed hashicorp/local v2.4.0 (signed by HashiCorp)
- Installing equinix/equinix v1.13.0...
- Installed equinix/equinix v1.13.0 (signed by a HashiCorp partner, key ID 1A65631C7288685E)
- Installing hashicorp/tls v4.0.4...
- Installed hashicorp/tls v4.0.4 (signed by HashiCorp)
Partner and community providers are signed by their developers.
If you'd like to know more about provider signing, you can read about it here:
https://www.terraform.io/docs/cli/plugins/signing.html
Terraform has created a lock file .terraform.lock.hcl to record the provider
selections it made above. Include this file in your version control repository
so that Terraform can guarantee to make the same selections by default when
you run "terraform init" in the future.
Terraform has been successfully initialized!
You may now begin working with Terraform. Try running "terraform plan" to see
any changes that are required for your infrastructure. All Terraform commands
should now work.
If you ever set or change modules or backend configuration for Terraform,
rerun this command to reinitialize your working directory. If you forget, other
commands will detect it and remind you to do so if necessary.
1. Create a Terraform plan¶
The terraform plan command creates an execution plan, which lets you preview the changes that Terraform plans to make to your infrastructure.
Expected output:
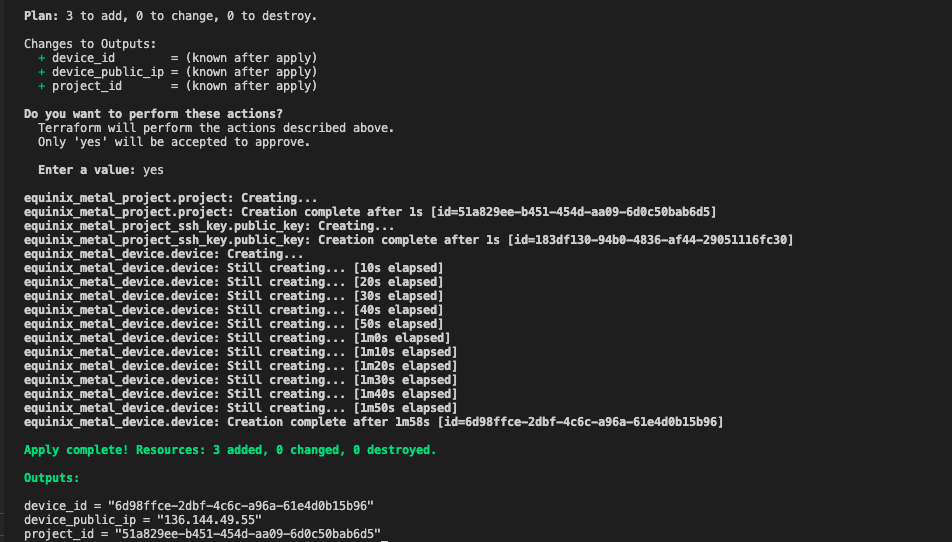
2. Terraform apply¶
The terraform apply command executes the actions proposed in a Terraform plan.
Enter yes when prompted for input.
Expected output:
3. Verify the server was provisioned¶
Take the project_id from the terraform apply and use metal CLI to check the status of the new server
Expected output:
Bash
$ export METAL_PROJECT_ID=$(terraform output --raw project_id)
$ metal devices get
+--------------------------------------+-----------+------------------+--------+----------------------+
| ID | HOSTNAME | OS | STATE | CREATED |
+--------------------------------------+-----------+------------------+--------+----------------------+
| 6d98ffce-2dbf-4c6c-a96a-61e4d0b15b96 | tf-device | Ubuntu 22.04 LTS | active | 2023-03-17T11:21:12Z |
+--------------------------------------+-----------+------------------+--------+----------------------+
4. SSH into the server¶
Now you can SSH login into the server:
Discussion¶
Before proceeding to the next part let's take a few minutes to discuss what we did. Here are some questions to start the discussion.
- How does Terraform keep track of my infrastructure changes?
- Can I scale up or replicate my device to another location without duplicating code?